What to Prioritize for a Secure Password Strategy
Securing your accounts against unauthorized access begins with the implementation of a strong password. It’s crucial to recognize that not all passwords offer the same level of protection. Here are five essential guidelines to ensure the security of your accounts.
Emphasize Complexity
The strength of a robust password hinges on its complexity. Avoid easily predictable combinations like “123456” or “password.” Instead, construct a password that incorporates a mix of uppercase and lowercase letters, numbers, and special characters. This complexity significantly boosts the resilience of your password, rendering it more resistant to brute-force attacks.
Adopt Unique Passwords for Each Account
Reusing passwords across multiple accounts poses a common yet perilous risk. Should one account be compromised, all interconnected accounts become susceptible. To mitigate this risk, generate distinctive passwords for each online account. Utilizing a reputable password manager can assist in organizing and securely storing these intricate combinations.
Prioritize Length
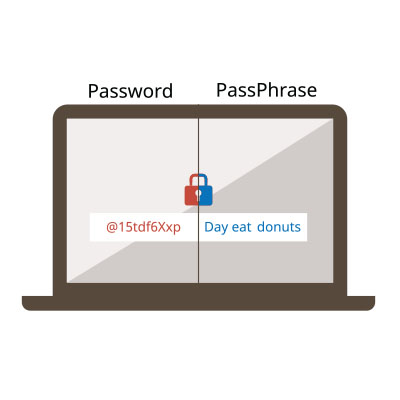
Generally, longer passwords offer greater security. Aim for a minimum of 12 characters and, when possible, opt for even longer passwords. Extended passwords create a more extensive search space, heightening the challenge for attackers to crack them. Consider using a passphrase—a sequence of words or a sentence—for both lengthy and memorable passwords.
Regularly Update Your Passwords
Given the dynamic nature of the digital landscape and evolving cyberthreats, it is crucial to regularly update your passwords. Establish a routine to change passwords every three to six months, or sooner if a security breach is reported on a platform you use. This straightforward yet effective practice significantly reduces the risk of unauthorized access to your accounts.
Enable Two-Factor Authentication (2FA)
Two-factor authentication (2FA) provides an additional layer of security by demanding a second form of verification alongside your password. This typically involves receiving a code on your mobile device or email, which you must enter after inputting your password. Even if a malicious actor obtains your password, the second factor is essential for gaining access. Activate 2FA whenever possible to fortify your account security.
For expert guidance in formulating your organization’s cybersecurity strategy, contact our knowledgeable consultants today at (603) 889-0800.

