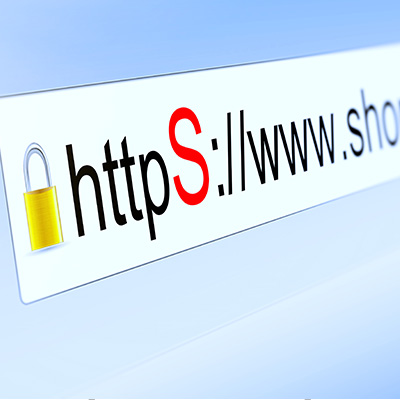
Encryption Implementing strong encryption protocols works to secure data during transmission. From a technical point of view: SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols are commonly used to encrypt communication between a user’s browser and a website. This added encryption ensures that any information exchanged is secure and cannot be easily intercepted by people looking to intercept it.
Understanding Browser Hijacking Attacks Browser hijacking attacks involve the stealthy installation of malicious software onto a user’s web browser. This malware can range from adware and spyware to more sophisticated forms like ransomware and keyloggers. The primary goal of these attacks is to gain unauthorized access to sensitive information or disrupt the user’s browsing experience.
Advantages Enhanced Security – Password managers excel in generating robust, unique passwords for each account, diminishing the threat of security breaches stemming from weak or reused passwords. Convenience – They offer a hassle-free means to store and automatically input login credentials, saving precious time and effort, with just one master password to remember. Organization – Password managers systematically arrange your passwords, ensuring easy retrieval and access to login information as needed. Multi-Device Accessibility – Many password managers feature apps or browser extensions that synchronize your passwords across various devices, guaranteeing uninterrupted access to your login details. Multi-Factor Authentication (MFA) – Certain password managers facilitate MFA integration, bolstering account security with an additional layer of protection. Password Audit – They possess the ability to scrutinize your existing passwords, identifying weaknesses or compromises and suggesting updates, thereby bolstering overall security. Encrypted Data – The majority of password managers employ robust encryption protocols to safeguard your data, rendering unauthorized access to your passwords exceedingly difficult. Password Sharing – Many password managers enable secure sharing of passwords with trusted individuals or team members without divulging the actual password.
In an individual sense, at least, it?s relatively simple. You don?t want to share anything more than what you need to. However, there is also something to be said for security and its relationship with privacy, and whether or not you should sacrifice one to maintain the other. You don?t have to pick one; in fact, you should be using security to protect your data privacy. Today, we?re investigating how you can do just that.
The Simple Fact is that Ransomware Hurts in Many Ways Let?s walk through what a modern ransomware attack might look like, acknowledging all the ways that the affected business would suffer as a result of the infection.