Don’t Get Hooked: Spotting Phishing Emails Before They Reel You In

From the classic Nigerian Prince emails to the cleverly crafted fake invoice, malicious digital correspondence is a constant threat to a business. It’s not just about losing a few bucks, either. A successful phishing attack can cripple your operations, compromise sensitive data, and even lead to your company’s demise.
So, how do you spot these digital dangers? Here are some of the most obvious signs that a message is a wolf in sheep’s clothing:
The Urgent, Demanding, or Threatening Tone
You get a message and it reads: “Your account will be suspended immediately if you don’t click this link!” “Urgent action required: Payment overdue!” “Failure to respond will result in legal action.”
Scammers thrive on panic. They want you to act without thinking, to bypass your usual critical analysis. They create a sense of urgency to prevent you from double-checking the sender or scrutinizing the link. This is a classic social engineering tactic designed to exploit human fear and a desire to avoid negative consequences.
Generic Greetings and Impersonal Language
A greeting like: “Dear Valued Customer,” “Hello User,” “To Whom It May Concern.” Even if it uses your company name, if it doesn’t address you personally, be wary.
Mass phishing campaigns often use generic greetings because they don’t know the recipient’s name. A legitimate company or contact will almost always address you by name. This lack of personalization is a strong indicator that the sender doesn’t have a genuine relationship with you or your organization.
Spelling, Grammar, and Punctuation Errors
Bad grammar—such as numerous typos, awkward phrasing, incorrect capitalization, and missing punctuation—is a giant red flag.
While everyone makes mistakes, legitimate businesses usually have professional copywriters and proofreaders for their official communications. A high volume of errors often points to a scammer who isn’t a native speaker or who is simply being careless because they’re sending out thousands of similar messages. It’s a clear sign of unprofessionalism and a lack of credibility.
Suspicious Sender Email Address or Display Name Mismatch
If you get an email from Microsoft but the sender’s address is su*****@***************ft.ru, or a display name like CEO’s Name but the actual email address is ra*******@***il.com, you will definitely need to be careful.
This is one of the most crucial checks. Scammers often try to spoof email addresses or create very similar-looking ones to trick you. Always hover over (but don’t click!) the sender’s email address to reveal the true domain. If it doesn’t match the legitimate organization you expect, it’s almost certainly a scam. This is a direct attempt to impersonate a trusted source.
Links to Unfamiliar or Suspicious Websites
If a link in the message promises to take you to your bank, but the URL is mybank.xyz.co instead of mybank.com. Or a link that’s just a string of random characters.
Clicking a malicious link is like opening the door to a thief. It can lead to malware downloads, credential harvesting pages (where you’re tricked into entering your login details), or drive-by downloads. Always hover over links to see the actual URL before clicking. If it looks fishy, don’t click it!
Requests for Sensitive Information
You get a message asking you to verify your password, Social Security number, credit card details, or other personal identifying information (PII). These are almost always a scam unless you are actively engaged with an organization.
Legitimate organizations, especially banks and government agencies, will never ask you for sensitive information, such as passwords, via email. They already have it, or they’ll direct you to a secure portal for updates. These requests are almost always an attempt to steal your credentials or identity.
Unexpected Attachments
You get an email from an unknown sender with an attachment, or an attachment from a known sender that you weren’t expecting can get people caught off-guard.
Malicious attachments are a primary vector for malware, including ransomware. Opening these files can unleash viruses, trojans, and other destructive programs onto your system and network. Always be cautious with attachments, especially those that are unexpected or from unfamiliar sources.
The Real Dangers to Your Business
Here’s an illustration of a typical phishing email’s red flags:
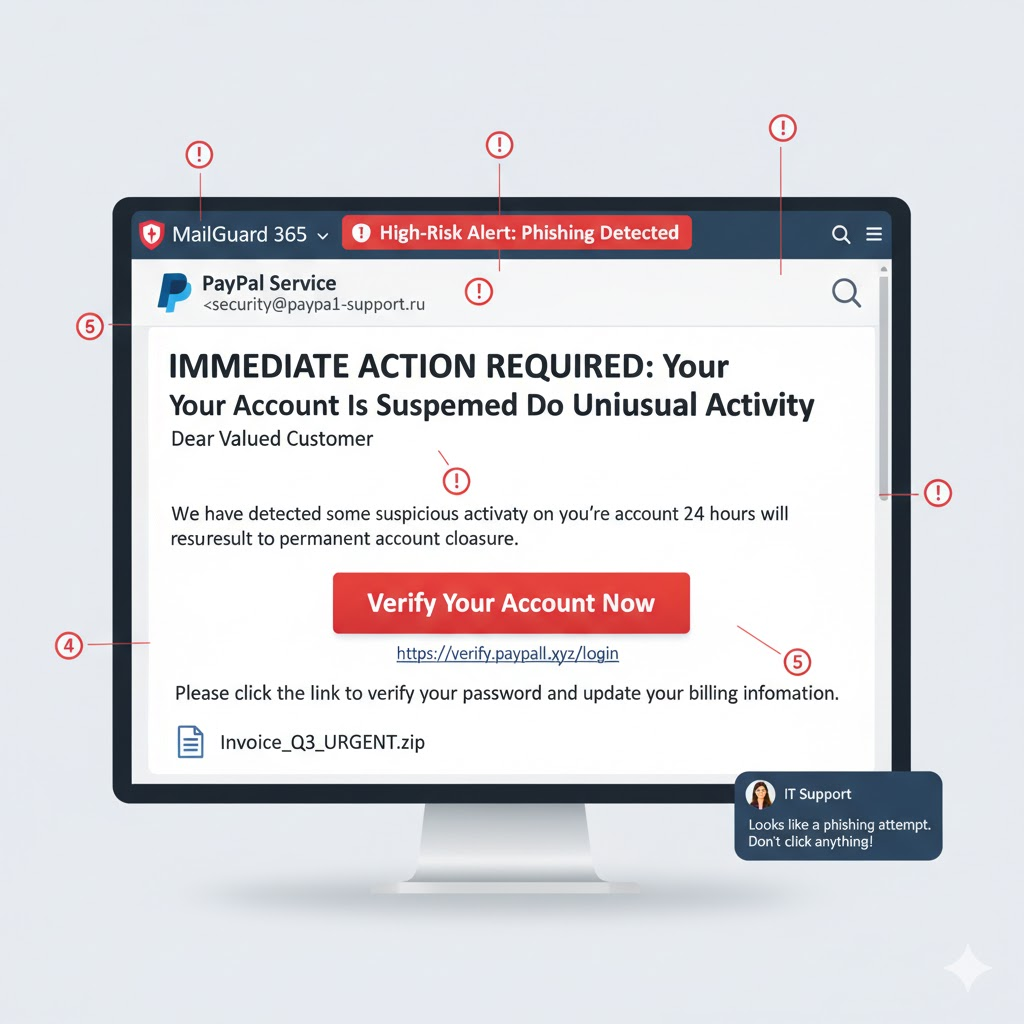
These scams aren’t just an annoyance; they pose existential threats:
- Financial loss – Direct theft of funds, fraudulent transactions, or ransomware demands.
- Data breach – Compromise of customer data, intellectual property, or employee PII, leading to regulatory fines, reputational damage, and loss of trust.
- Operational disruption – System downtime, network outages, and loss of access to critical data due to malware infections.
- Reputational damage – Loss of customer confidence, negative publicity, and a tarnished brand image that can take years to rebuild.
- Legal and compliance issues – Fines, lawsuits, and a failure to meet industry regulations (e.g., GDPR, HIPAA).
What You Can Do
Education is your first line of defense. Train your employees to recognize these signs. Implement strong email filters and antivirus software. Use multi-factor authentication (MFA) wherever possible, and remember, when in doubt, delete it! If you’re unsure about an email, contact the sender directly through a known, legitimate channel (not by replying to the suspicious email).
Stay vigilant, stay safe, and let’s keep those digital sharks from circling your business. If you need help with your cybersecurity strategy, give the experts at White Mountain IT Services a call at (603) 889-0800.

